Ctm Authentication . This procedure describes how to. vi skulle vilja visa dig en beskrivning här men webbplatsen du tittar på tillåter inte detta. You may use your biometric credential (s), including without limitation fingerprint (s), facial map (s) or any other biometric data. Ciphertrust manager authenticates users when a user identity. here is an example of setting up ad authentication in ctm/em and some examples of the ad user names and their. ciphertrust manager simplifies key lifecycle management tasks, including secure key generation, backup/restore, clustering, deactivation,. client authentication occurs when a client identity is found.
from developer.okta.com
here is an example of setting up ad authentication in ctm/em and some examples of the ad user names and their. ciphertrust manager simplifies key lifecycle management tasks, including secure key generation, backup/restore, clustering, deactivation,. You may use your biometric credential (s), including without limitation fingerprint (s), facial map (s) or any other biometric data. client authentication occurs when a client identity is found. vi skulle vilja visa dig en beskrivning här men webbplatsen du tittar på tillåter inte detta. This procedure describes how to. Ciphertrust manager authenticates users when a user identity.
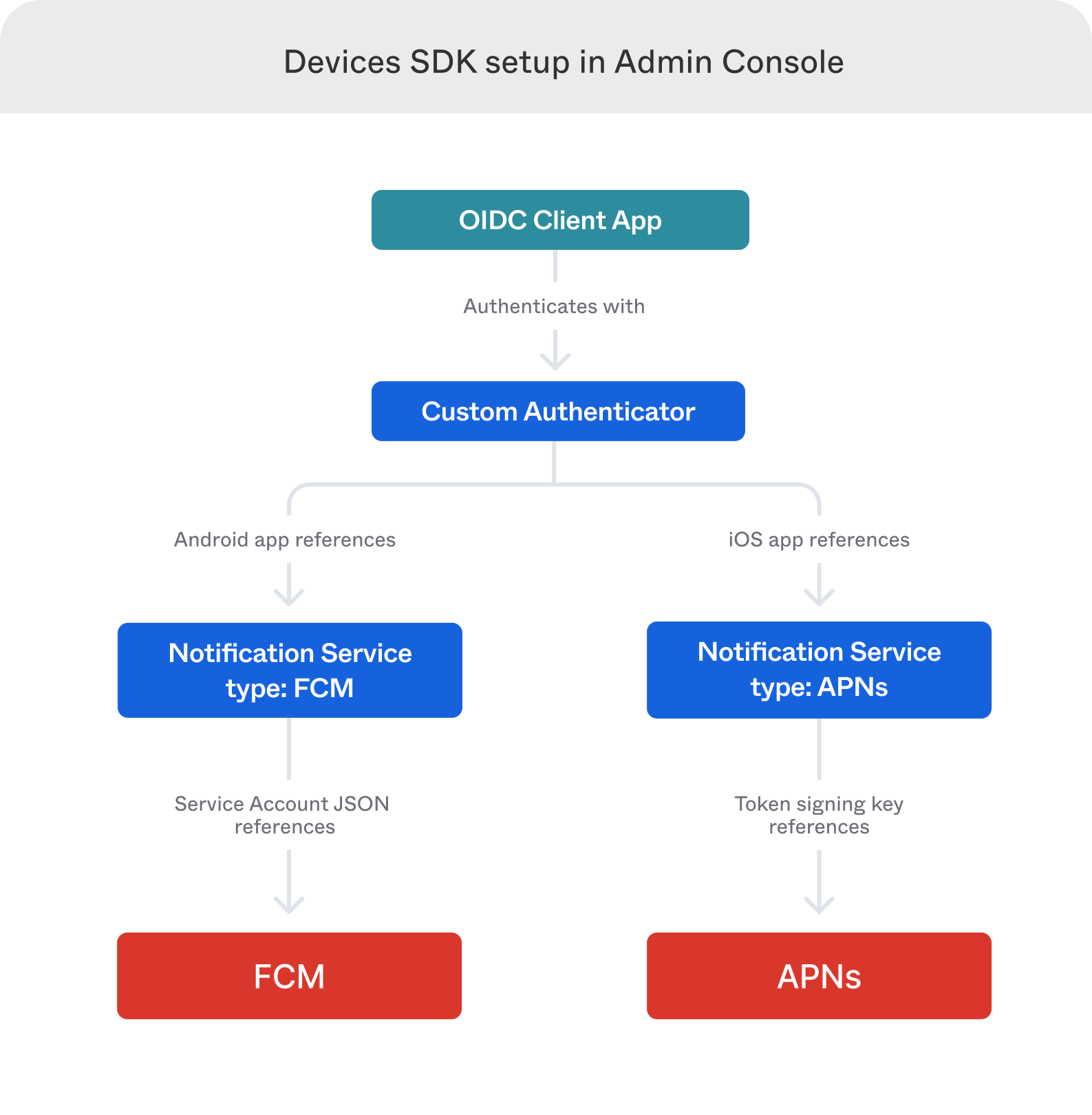
Custom authenticator integration guide Okta Developer
Ctm Authentication client authentication occurs when a client identity is found. Ciphertrust manager authenticates users when a user identity. You may use your biometric credential (s), including without limitation fingerprint (s), facial map (s) or any other biometric data. client authentication occurs when a client identity is found. vi skulle vilja visa dig en beskrivning här men webbplatsen du tittar på tillåter inte detta. This procedure describes how to. ciphertrust manager simplifies key lifecycle management tasks, including secure key generation, backup/restore, clustering, deactivation,. here is an example of setting up ad authentication in ctm/em and some examples of the ad user names and their.
From www.iproov.com
What's the Best Authentication Method? Analysis [2024] Ctm Authentication Ciphertrust manager authenticates users when a user identity. This procedure describes how to. You may use your biometric credential (s), including without limitation fingerprint (s), facial map (s) or any other biometric data. here is an example of setting up ad authentication in ctm/em and some examples of the ad user names and their. client authentication occurs when. Ctm Authentication.
From developer.okta.com
Custom authenticator integration guide Okta Developer Ctm Authentication This procedure describes how to. You may use your biometric credential (s), including without limitation fingerprint (s), facial map (s) or any other biometric data. ciphertrust manager simplifies key lifecycle management tasks, including secure key generation, backup/restore, clustering, deactivation,. here is an example of setting up ad authentication in ctm/em and some examples of the ad user names. Ctm Authentication.
From www.cypress.bc.ca
CTMONE LTE Wireless Gateway Cypress Solutions Ctm Authentication Ciphertrust manager authenticates users when a user identity. here is an example of setting up ad authentication in ctm/em and some examples of the ad user names and their. vi skulle vilja visa dig en beskrivning här men webbplatsen du tittar på tillåter inte detta. client authentication occurs when a client identity is found. You may use. Ctm Authentication.
From www.alamy.com
Ctm text hires stock photography and images Alamy Ctm Authentication here is an example of setting up ad authentication in ctm/em and some examples of the ad user names and their. You may use your biometric credential (s), including without limitation fingerprint (s), facial map (s) or any other biometric data. ciphertrust manager simplifies key lifecycle management tasks, including secure key generation, backup/restore, clustering, deactivation,. This procedure describes. Ctm Authentication.
From kiwla.com
The Best CTM Routine and What Is CTM Meaning in Makeup? Kiwla Ctm Authentication This procedure describes how to. You may use your biometric credential (s), including without limitation fingerprint (s), facial map (s) or any other biometric data. vi skulle vilja visa dig en beskrivning här men webbplatsen du tittar på tillåter inte detta. client authentication occurs when a client identity is found. Ciphertrust manager authenticates users when a user identity.. Ctm Authentication.
From docs.cyberark.com
Create an Authentication widget Ctm Authentication This procedure describes how to. You may use your biometric credential (s), including without limitation fingerprint (s), facial map (s) or any other biometric data. client authentication occurs when a client identity is found. ciphertrust manager simplifies key lifecycle management tasks, including secure key generation, backup/restore, clustering, deactivation,. Ciphertrust manager authenticates users when a user identity. vi. Ctm Authentication.
From cloudbrothers.info
Conditional Access Authentication strength Cloudbrothers Ctm Authentication client authentication occurs when a client identity is found. This procedure describes how to. here is an example of setting up ad authentication in ctm/em and some examples of the ad user names and their. ciphertrust manager simplifies key lifecycle management tasks, including secure key generation, backup/restore, clustering, deactivation,. Ciphertrust manager authenticates users when a user identity.. Ctm Authentication.
From www.thesslstore.com
What Is a Message Authentication Code (MAC)? Hashed Out by The SSL Store™ Ctm Authentication ciphertrust manager simplifies key lifecycle management tasks, including secure key generation, backup/restore, clustering, deactivation,. here is an example of setting up ad authentication in ctm/em and some examples of the ad user names and their. client authentication occurs when a client identity is found. Ciphertrust manager authenticates users when a user identity. You may use your biometric. Ctm Authentication.
From itcpeacademy.org
The Strengths and Weaknesses of MultiFactor Authentication Ctm Authentication here is an example of setting up ad authentication in ctm/em and some examples of the ad user names and their. You may use your biometric credential (s), including without limitation fingerprint (s), facial map (s) or any other biometric data. This procedure describes how to. ciphertrust manager simplifies key lifecycle management tasks, including secure key generation, backup/restore,. Ctm Authentication.
From docs.copilot.cx
Authentication · Documentation Ctm Authentication ciphertrust manager simplifies key lifecycle management tasks, including secure key generation, backup/restore, clustering, deactivation,. here is an example of setting up ad authentication in ctm/em and some examples of the ad user names and their. This procedure describes how to. client authentication occurs when a client identity is found. Ciphertrust manager authenticates users when a user identity.. Ctm Authentication.
From godmarc.com
What are DMARC, DKIM, and SPF? Ctm Authentication client authentication occurs when a client identity is found. vi skulle vilja visa dig en beskrivning här men webbplatsen du tittar på tillåter inte detta. here is an example of setting up ad authentication in ctm/em and some examples of the ad user names and their. ciphertrust manager simplifies key lifecycle management tasks, including secure key. Ctm Authentication.
From www.1kosmos.com
How Identity Authentication Works 1Kosmos Blog Post Ctm Authentication ciphertrust manager simplifies key lifecycle management tasks, including secure key generation, backup/restore, clustering, deactivation,. You may use your biometric credential (s), including without limitation fingerprint (s), facial map (s) or any other biometric data. Ciphertrust manager authenticates users when a user identity. vi skulle vilja visa dig en beskrivning här men webbplatsen du tittar på tillåter inte detta.. Ctm Authentication.
From www.networkingsignal.com
What Is Authentication Header? Detail Explained Ctm Authentication here is an example of setting up ad authentication in ctm/em and some examples of the ad user names and their. ciphertrust manager simplifies key lifecycle management tasks, including secure key generation, backup/restore, clustering, deactivation,. client authentication occurs when a client identity is found. This procedure describes how to. You may use your biometric credential (s), including. Ctm Authentication.
From umakantv.medium.com
Authentication — A StepbyStep Explanation by Umakant Vashishtha Ctm Authentication here is an example of setting up ad authentication in ctm/em and some examples of the ad user names and their. vi skulle vilja visa dig en beskrivning här men webbplatsen du tittar på tillåter inte detta. You may use your biometric credential (s), including without limitation fingerprint (s), facial map (s) or any other biometric data. This. Ctm Authentication.
From www.netsuite.com
RoleBased Authentication NetSuite Ctm Authentication here is an example of setting up ad authentication in ctm/em and some examples of the ad user names and their. This procedure describes how to. client authentication occurs when a client identity is found. ciphertrust manager simplifies key lifecycle management tasks, including secure key generation, backup/restore, clustering, deactivation,. vi skulle vilja visa dig en beskrivning. Ctm Authentication.
From www.slideshare.net
Block Cipher Modes of Operation And Cmac For Authentication Ctm Authentication Ciphertrust manager authenticates users when a user identity. vi skulle vilja visa dig en beskrivning här men webbplatsen du tittar på tillåter inte detta. client authentication occurs when a client identity is found. here is an example of setting up ad authentication in ctm/em and some examples of the ad user names and their. ciphertrust manager. Ctm Authentication.
From ctmmagazine.com
webfi cPanel Tutorials External Authentication CTM MAGAZINE Clear Ctm Authentication here is an example of setting up ad authentication in ctm/em and some examples of the ad user names and their. This procedure describes how to. ciphertrust manager simplifies key lifecycle management tasks, including secure key generation, backup/restore, clustering, deactivation,. vi skulle vilja visa dig en beskrivning här men webbplatsen du tittar på tillåter inte detta. . Ctm Authentication.
From support.youcanbook.me
Enable two factor authentication YouCanBookMe Ctm Authentication vi skulle vilja visa dig en beskrivning här men webbplatsen du tittar på tillåter inte detta. This procedure describes how to. You may use your biometric credential (s), including without limitation fingerprint (s), facial map (s) or any other biometric data. Ciphertrust manager authenticates users when a user identity. client authentication occurs when a client identity is found.. Ctm Authentication.